When you want to streamline your ability to release or update products quickly, integrating DevOps into your organization can prove to be well worth any changes that need to be made in order to implement the new practices. One of the biggest advantages to DevOps is what is often called velocity - working with both speed and direction. By breaking down barriers between IT and business, this close and speedy collaboration can provide the direction that propels your business forward.
First Order: CollaborationThere is clear evidence to suggest that a DevOps approach to tech development can have a significant impact on the velocity of an IT organization.
Source: Chris Cancialosi, Forbes
When people can directly collaborate, they tend to hash out any potential issues with a project much more quickly. Organizations the are separated by function may find that development on a project moves much more slowly than hoped.
For example, selected business team members might meet with selected IT members at the beginning of a project. They then each go their own way with expectations that may change before their next meeting, which could be after several weeks, months, or longer have passed.

The intersection of various departments as DevOps. Source: Wikipedia
On the other hand, employing DevOps allows for the more collaborative function between teams. There can be employees from each group that meets daily or team members from one group embedded within one or more other groups so that the different functional groups are all working directly with one another each and every day.
This allows for communication of any new needs or issues to happen right away, where differences can be hashed out immediately, rather than waiting for a meeting that could be derailed by one issue like this for the entire meeting duration and being unable to address other needs and concerns during that precious time.
DevOps helps the relationship between Development and Operations, the relationship between IT and the business, and the relationship between the company and its customers and employees.
Source: DEVOPS digest
Development with VelocityDevOps is often implemented when an organization uses the agile method of software development, which often leads to the need for the actual organizational changes that lead to beginning to use DevOps practices.
The good news is that in recent years there are two healthy and related trends in the Agile community: continuous delivery (CD) and DevOps.
Source: Scott W. Ambler, Dr. Dobbs
Agile development is a method that encourages speed and flexibility in response to an ever-changing set of requirements during software development. Instead of needing to wait for new ideas, this flexibility allows development to continue with little interruption or delay in the process as needs change. This ability to change rapidly also increases the number of releases of a product. Thus new releases and updates happen at a much faster rate, which encourages continuous delivery of a product.
The speed of agile typically requires a toolset that allows for the automation of certain processes so that speed is not hindered by processes that need to be performed manually over and over again. Not only can that be tedious, but it can use up the valuable time your developers or other IT staff could be using to further enhance the product and deliver further releases. Automation allows for many of the processes to be free of manual involvement, which frees up your staff for other work.
Our experience suggests, for instance, that companies can reduce the average number of days required to complete code development and move it into live production from 89 days to 15 days, a mere 17 percent of the original time.
Source: McKinsey & Company
When DevOps is employed alongside agile development to support it, your velocity will be increased even further and allow you to make your customers happier and do so more quickly!
Total VelocityWhile DevOps can be a challenge to get going as it requires a number of organizational changes tailored to your specific business needs, it can be well worth the effort needed to reorganize and regroup. The increased speed of delivery of your products and updates can really help you, especially if it helps you to be first to market on a new idea.
Not only will you get improved speed, but it can help your staff feel more like they are getting along and are contributing to projects that make it to completion. Seeing something they contributed to in action can be helpful in motivating staff to find ways to streamline processes even further and thus enhance your velocity that much more!






_original.jpg)

_original.jpg)







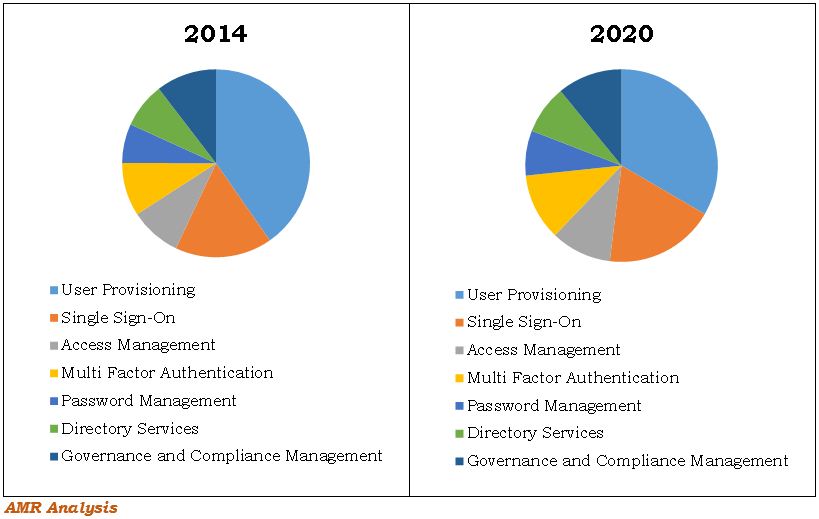 Multifactor authentication and single-sign on will account for larger shares of the global cloud identity access management market in 2020. Source:
Multifactor authentication and single-sign on will account for larger shares of the global cloud identity access management market in 2020. Source: